Path Search
Overview of the Path Search Exercise
The Path Search feature is a sophisticated tool that allows operators to conduct an in-depth analysis of network reachability and device behavior. It supports exploration of all possible network paths from any source to any destination, accommodating a variety of protocols, layer-4 ports, and packet header details. This functionality is crucial for understanding network traffic dynamics, identifying potential issues, and optimizing network performance.
Example mnemonics like f(internet)(tp_dst.HTTPS)z(delivered) can be pasted into the search bar to define a search.
Estimated Completion Time
20 minutes
Exercise and Steps
Clear the search bar when pasting new search patterns
Exercise 1: Open-Ended Search
Objective: Conduct an open-ended search to find all L4 destination ports that are deliverable from the Internet.
-
Search Input: Paste
f(internet)z(delivered)into the search bar.f(internet)z(delivered) -
Filter Utilization: Open the Filters component on the left to view all related headerspace information.
-
Examine headerspace filters
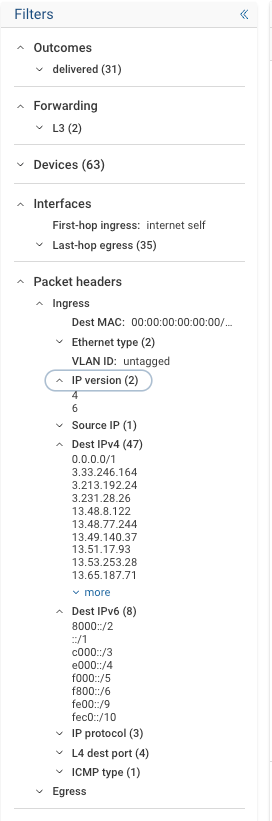
-
Adding L4-Dest-Port Filter
- Enhance the search by adding an
l4-dest-portfilter.
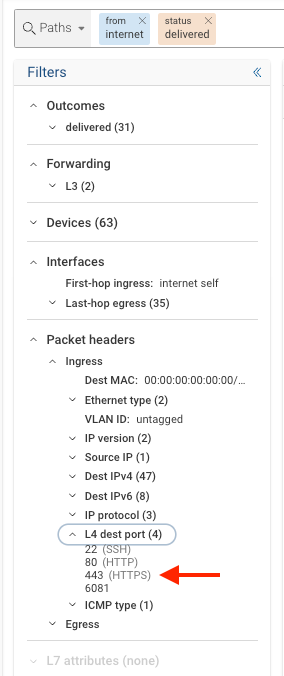
- Enhance the search by adding an
-
Search Modification: Notice the search bar has now changed with the updated L4 destination port filter
Notice that all (4) ports listed under L4 dest port are deliverable from the Internet
- Path Groups: Examine all the possible flows by toggling through the Path Groups
Observe the number of path groups identified.
Exercise 2: Specifying Dest-IP Filter
Objective: In this exercise we will refine our search to filter all paths with a destination IP
-
Search Refinement: Copy and Paste the following into the search bar
f(internet)(tp_dst.443)(ipv4_dst.190.37.14.120)z(delivered) -
Alternate Path Selection: For hop
atl-isp-edge-01, click on the device name and selectthrough atl-isp-edge02for an alternate path.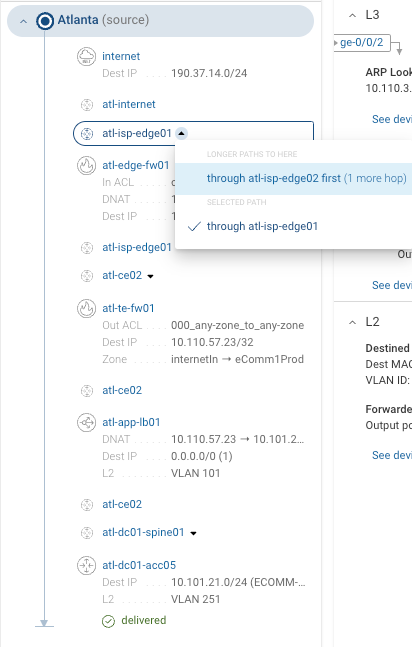
-
Policy Review: At hop
atl-edge-fw-01, examine the ACL and NAT policies. Notice the normalization of data and the highlighted relevant lines in the policy?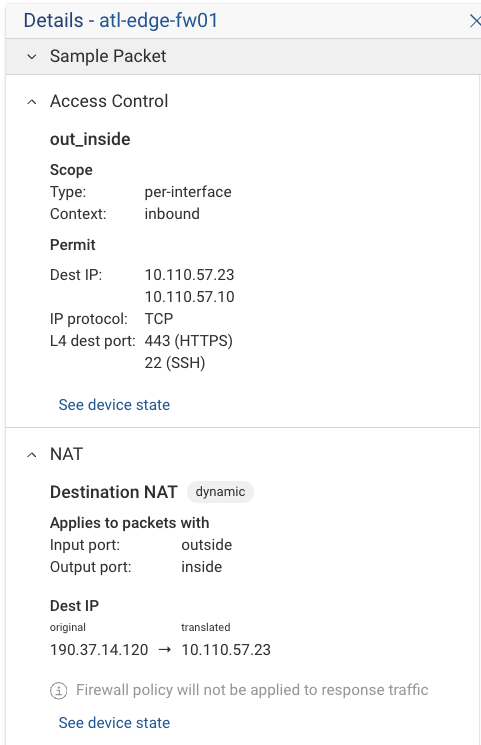
Exercise 3: Using To Instead of Dest-IP
Objective: Compare the results of using To versus Dest-IP in a search.
-
Initial Search: Copy below into the search bar
f(internet)t(10.101.10.3) -
Modified Search: Change the query to below and evaluate the difference
f(internet)(ipv4_dst.10.101.10.3)
Evaluate the results and differences between using To and Dest-ip. Consider if 10.101.10.3 should be reachable
from the internet.
See: Search Keywords
Exercise 4: Leveraging Bypass Mode
Objective: Test alternate paths by utilizing bypass mode.
-
Bypass Mode Activation: Copy below into search bar
f(internet)(ipv4_dst.190.37.14.120)(tp_dst.HTTPS)b(atl-dc01-spine01)z(delivered)
Exercise 5: Leveraging Permit-ALL Mode
Objective: Assess reachability and security outcomes using permit-all mode.
-
Permit-All Mode Search: Copy below into search bar
f(.nsx_vsw_host_001)(ipv4_dst.10.5.20.12)(tp_dst.22) -
Select Permit All Mode
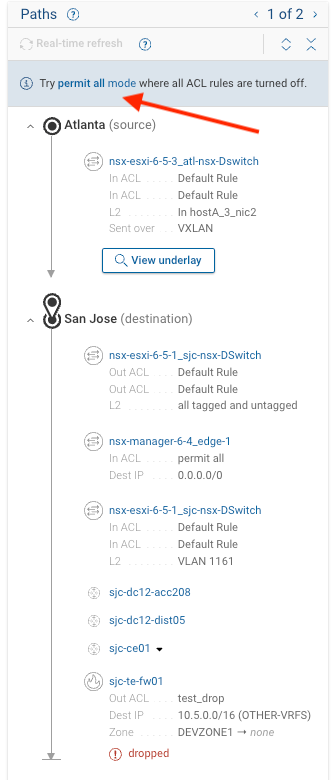
Note the bypass of firewall deny rules, allowing for continued reachability testing.
- Determine the reachability outcome and identify which firewalls were blocking the traffic.
Key Insights
- Detailed Exploration: Path Search facilitates a thorough examination of network paths, enhancing understanding of traffic flow and device behavior.
- Comprehensive Insight: The feature provides extensive information through interactive exploration, revealing underlying data and configurations.